The exploit database is a cve compliant archive of public exploits and corresponding vulnerable software developed for use by penetration testers and vulnerability researchers.
Employee timeclock software exploit.
Free time clock calculator clock in clock out time duration calculator.
Ontheclock is 100 web based and trusted by more than 10 000 companies with a 4 8 star rating.
An employee time clock system that offers a powerful and accurate solution for small businesses to track in house and remote employee hours worked for payroll.
Our online time clock calculator is commonly used by small business owners who cannot yet afford a time clock software system.
Employee timeclock software 0 99 sql injection.
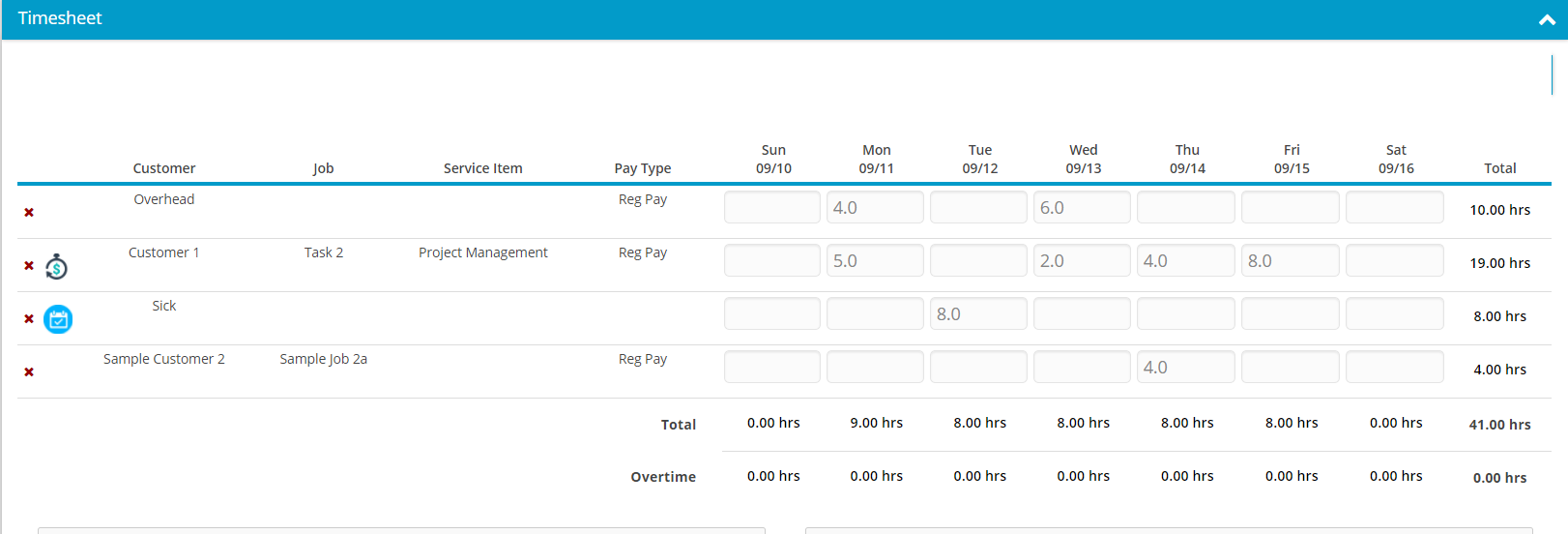
Time clock software is the system that is used by organizations to record the working hours of employees.
Employee timeclock software free.
Security vulnerabilities of timeclock software employee timeclock software version 0 99 list of cve security vulnerabilities related to this exact version.
If we compare the time clock software with the time attendance software and the time tracking software then the only difference is the feature for.
You can filter results by cvss scores years and months.
The google hacking database ghdb is a categorized index of internet search engine queries designed to uncover interesting and usually sensitive information made publicly.
It has functionalities of employee scheduling leave management task management pto etc.
The exploit database is a repository for exploits and proof of concepts rather than advisories making it a valuable resource for those who need actionable data right away.
Free software for employees to use as a timeclock.
Employee timeclock software 0 99 places the database password on the mysqldump command line which allows local users to obtain sensitive information by listing the process.
Secunia research has discovered some vulnerabilities in employee timeclock software which can be exploited by malicious people to conduct sql injection attacks.
An employee time and attendance system keeps track of when your employees sign in and out of work.
This page provides a sortable list of security vulnerabilities.
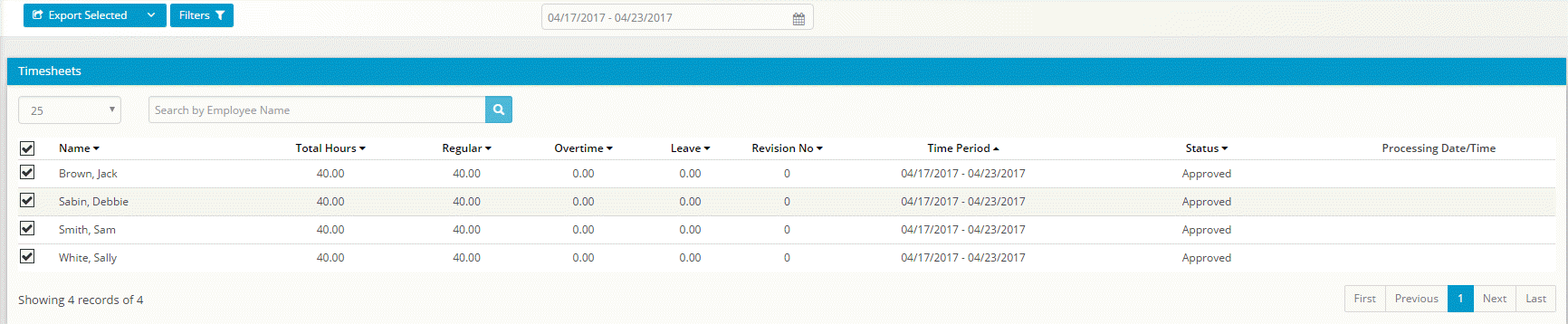
This information can then be compiled to produce the total hours worked and the amount that the employees should be paid.